At the Intersection of Hydropower and Cybersecurity
The New Tool That Could Advance Hydropower Plant Cybersecurity Through Artificial Intelligence

In the world of cybersecurity, they say a cyberattacker only needs one win, but a security team needs to win 100% of the time to keep a system safe.
Achieving that level of protection is the aim of a new, specially designed cybersecurity tool for hydropower plants that is now in development at the National Renewable Energy Laboratory (NREL). Enter: the data-driven and hardware-agnostic Cybersecurity Situational Awareness Tool for Hydropower, or CYSAT-Hydro.
This tool is emerging amid two significant storylines in the energy world. The first is the rapid growth of internet-connected distributed energy resources that can be integrated with large generation sources like hydroelectric plants and could create cybersecurity risks for those plants’ digital interfaces on the grid. The second is several high-profile cyberattacks targeting energy systems in recent years. Notably, the May 2021 ransomware attack on the Colonial Pipeline not only cost the pipeline’s operators millions of dollars but also wreaked havoc on the gas supply for millions of Americans along the Eastern Seaboard.
“If you examine the past 10 to 15 years, there has been an increase in malicious and nation-sponsored actors attempting to hack and compromise critical infrastructure, such as the power grid, due to the significant impact and enormous monetary benefits,” said Vivek Kumar Singh, a senior cybersecurity researcher at NREL. Singh is part of the team that led the development of the CYSAT-Hydro tool.
Over the last decade, there has been a nationwide push to modernize the U.S. power grid. New technologies, such as smart meters, data aggregators, advanced communication infrastructure, wide-area control systems, and edge computing, are being used to better integrate clean energy sources.
Hydropower plants are part of the smart grid technology trend. Operators are increasingly integrating small hydropower facilities with energy storage systems to provide reliable power supply at a peak market rate.
A key application of smart grid technology is the use of hydropower-integrated battery energy storage systems to provide frequency regulation services. These types of integrated systems enable operators to access and communicate with the various grid components surrounding hydropower plants more easily, reducing operation costs for owners of hydropower assets.
Any digital space presents a potential opportunity for persistent hackers to access and compromise a network. CYSAT-Hydro is designed to protect those potential points of access to ensure the grid’s reliability.
While smart grid technologies increase the grid’s reliability, they could also create new attack surfaces for hackers to compromise the grid network.
“If you have so many data points and so much communication happening, it increases the attack surface and chances of a cyberattack,” Singh said.
Keeping Up With the Evolving Cybersecurity Landscape
The need to protect new potential points of access to the grid is why the U.S. Department of Energy’s Water Power Technologies Office supported the development of a new tool to enhance the cybersecurity and resilience of hydropower plants.
Many of the cyberattacks the grid could face are stealthy and require little knowledge of the grid itself to conduct. They could come in the form of denial-of-service attacks, in which the attacker may only require minimal information about the power system, such as an internet protocol (IP) address.
“As the grid becomes increasingly interconnected with numerous ‘Internet of Things’ devices, the threat of such attacks is growing tremendously,” Singh said.
Some of the potential cyberattacks targeting hydropower-integrated battery energy storage systems could include line tripping attacks and data integrity attacks on regulation signals. The former would involve unauthorized tripping of a relay to disconnect distribution power lines or loads, while the latter would involve modifying the incoming regulation signals to disrupt frequency regulation. The creators of CYSAT-Hydro looked at these types of attack vectors while developing the tool.
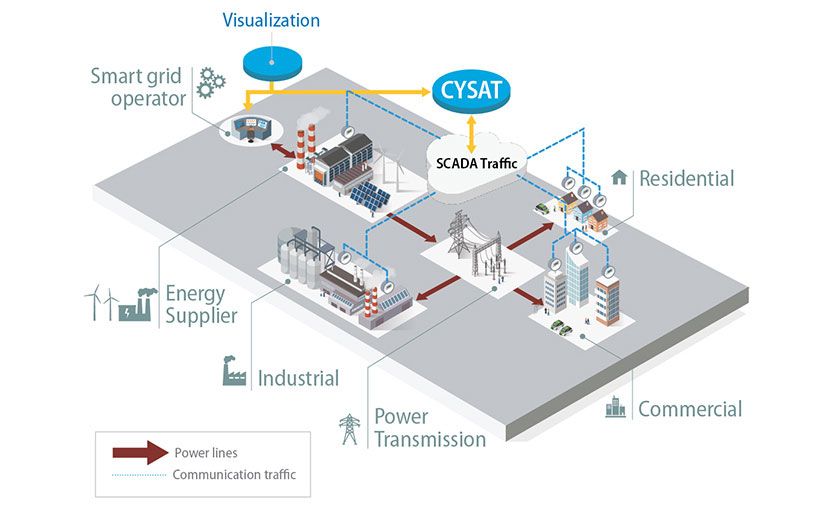
CYSAT-Hydro uses artificial intelligence to detect anomalies in the operational technology network that are often stealthily deployed. CYSAT-Hydro then sends detailed information about cyberattacks to system operators and analyzes grid performance in real time to help operators restore grid functionality after an attack. Beyond providing state-of-the-art cyberattack protection, CYSAT-Hydro also computes technical and economic grid performance metrics of various distributed energy resources. These metrics help grid operators understand the value of the CYSAT-Hydro tool.
“Think about the duration of a cyberattack and how much it could cost operators,” Singh said. “If an attack shut down a hydro plant for five hours, it might cost you a huge amount of money as the operator, and it could affect flood control and local water supplies and ecosystems. This tool would potentially circumvent any of those issues by helping prevent the attack in the first place.”
The tool supports a user-friendly application programming interface that is compatible across operating systems. It also features a real-time visualization dashboard that gives users a comprehensive view of grid operations, network traffic, and intrusions, among other data.
Taking Cybersecurity to the Next Level
Because CYSAT-Hydro will be made open source and publicly available, it can be broadly deployed more easily. It can also be applied to other grid technologies and other critical infrastructures outside of the power grid, such as water and gas pipelines.
“This tool is completely data-oriented, meaning if you have an understanding of what happened during a cyberattack and where it happened, you could apply this tool to other supervisory control and data acquisition systems outside of hydroelectric facilities,” Singh said.
As the development of CYSAT-Hydro reaches its final stages, Singh hopes that the tool’s adaptability will enable future growth.
“We are looking for potential field demonstration and technology commercialization in partnership with industry vendors and utilities. Further, we plan to continue working on this tool’s development with more case studies to improve its functionality,” Singh said. “When we give our final update to the Water Power Technologies Office, we will also look into what we can do with CYSAT-Hydro next to advance the state of cybersecurity for clean energy systems.”
Learn more about how NREL’s experts are helping advance hydropower. And subscribe to the NREL water power newsletter, The Current, for the latest news on NREL's water power research.
Last Updated May 28, 2025
