Critical Energy Cybersecurity Accelerator: Cohort 2
NLR’s Critical Energy Cybersecurity Accelerator (CECA) sought to address the inherent physical and technological breadth, variation, and complexity of industrial control systems (ICS) with Cohort 2.
The CECA program is in partnership with the U.S. Department of Energy’s Office of Cybersecurity, Energy Security, and Emergency Response and utilities.
As market forces drive the electric sector to build a smarter grid powered by renewable energy, digital technologies enable innovative operational models through advanced monitoring and control in industrial control systems.

Cybersecurity is a complex field full of unique challenges. Threats, system architectures, and technologies will continue to evolve as the energy sector undergoes significant transformations at an increasing pace. Solutions such as the runZero and Asimily products tested by CECA in Cohort 2 can help to identify control system assets and to monitor changes in equipment, which can improve the security of the sector as a whole.
ICS networks often contain a rich mix of devices developed by multiple vendors over a substantial range of time. Such technological diversity limits asset owner visibility into systems. Cohort 2 evaluated solutions designed to identify risks posed by the lack of visibility into ICS and tested the ability of solutions to improve asset owners’ ability to accurately identify known and unknown devices that are connected to their system at any time.
Solutions tested in CECA Cohort 2 are designed to improve "visibility" into ICS systems or device configurations. Testing evaluated both the ability of solutions to improve asset owner visibility into system or device configurations and the impact of the solution on system processes. The latter specifically addresses lingering industry concerns about the potential for active scanning to impact ICS processes and subsequent reliance on limited passive discovery.
In the News
Second Cohort of Critical Energy Cybersecurity AcceleratorEvaluates System Visibility, NLR News (2024)
Second Critical Energy Cybersecurity AcceleratorCohort Evaluates Solutions That Uncover Hidden Risks on Utility Networks, NLR News (2024)
Asimily Joins Second Cohort of Clean Energy Cybersecurity Accelerator, NLR News (2024)
The first report from CECA Cohort 2 evaluates the runZero product, a highly configurable tool that discovers information about individual assets and displays detailed information about each device in an ICS environment. The second report from CECA Cohort 2 evaluates the Asimily product, a suite of data-intensive tools that use passive sampling to expand insight into networked devices and understand anomalies and risks in the underlying system.
The runZero and Asimily public reports detail the Cohort 2 theme, the solutions, and the evaluations performed, and summarizes key conclusions and insights from the testing. Below is a summary of the key takeaways from both reports.
Access the CECA Evaluation GitHub Repository.
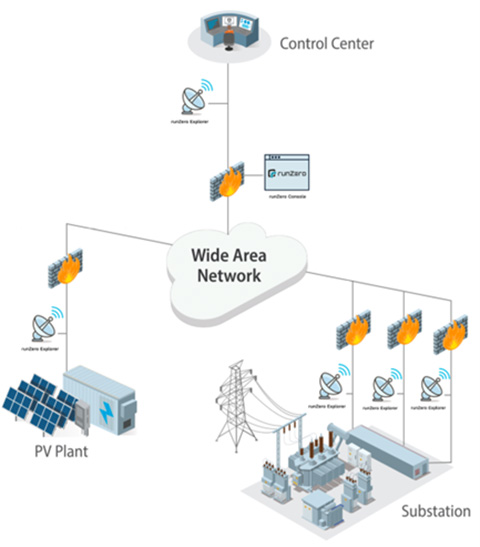
runZero
The runZero products comprise a highly configurable tool that uses deployed programs and a server-based user interface to discover information about individual assets and to compile a detailed, real-time assessment of each device in an ICS environment. CECA evaluation of the runZero product showed that it found all devices in the environment except for those which were not IP-addressable (i.e., connected to a remote terminal unit via serial). The runZero product is one of a class of solutions designed to improve an asset owner's visibility into their environment without impeding system operations. This improved visibility subsequently enhances risk assessment and appraisal.
CECA tested the runZero product against multiple ICS protocols and devices to validate applicability of the conclusions to the greatest degree possible. Although the testing results are not universally generalizable, CECA’s conclusions challenge concerns with active scanning in today's energy systems (see full report for discussion and citations). Active scanning in the CECA test environment proved safe, opening the door to expand scanning beyond passive collection methods.
Conclusions from CECA’s evaluations indicate multiple benefits for industry:
- Active scanning provides a richer set of data about the connected devices than passive discovery.
- Active scanning in the CECA operational technology environment improved visibility without impact on system performance or disruption of ICS assets or ongoing supervisory control and data acquisition processes and communications.
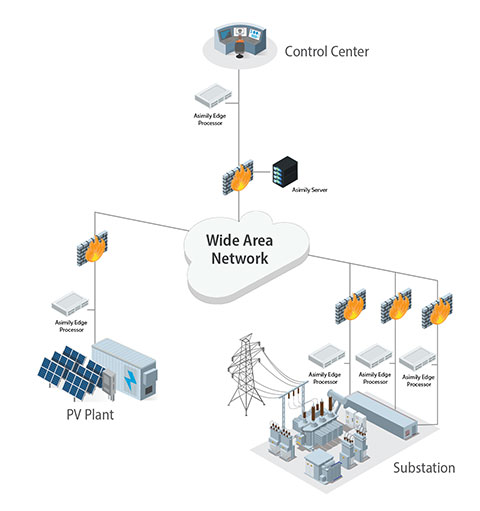
Asimily
The Asimily solution employs passive sampling of network traffic to identify devices. This approach seeks to improve visibility into connected devices by enhancing capabilities related to inventorying devices, mitigating device vulnerabilities, modeling risks, detecting threats, and responding to incidents. The solution is deployed locally to provide visibility into all information technology, operational technology, and Internet-of-Things traffic.
CECA’s evaluations showed that the Asimily solution identified information about many of the devices in the environment, and the risks posed to those devices. CECA also tested Asimily’s experimental targeted active scanning. Tests demonstrated that, while this capability enhances visibility into networked devices, it may not be suited to production environments where 100% availability is required.
Conclusions from CECA’s evaluations highlight two challenges remaining for industry:
- Visibility of assets connected via legacy media like serial and assets that are not IP-addressable
- Visibility into assets connected behind a remote terminal unit that does not forward traffic to subordinate devices.
Download the Asimily Public Report.
Subscribe To Learn More
Subscribe to receive CECA email updates related to current and future cohorts.
Subscribe to NLR's Energy Systems Integration newsletter for monthly updates on energy security and resilience.
Contact
Contact the Critical Energy Cybersecurity Accelerator program administrator with questions.
Share
Last Updated Dec. 7, 2025
